This is part one of a three-part series on website security.
I’m difficult to remember and impossible to guess. I protect your identity and your money. I should never be written down or spoken aloud. I come in many variations but exist only for you. I am lettered and full of characters.
What am I?
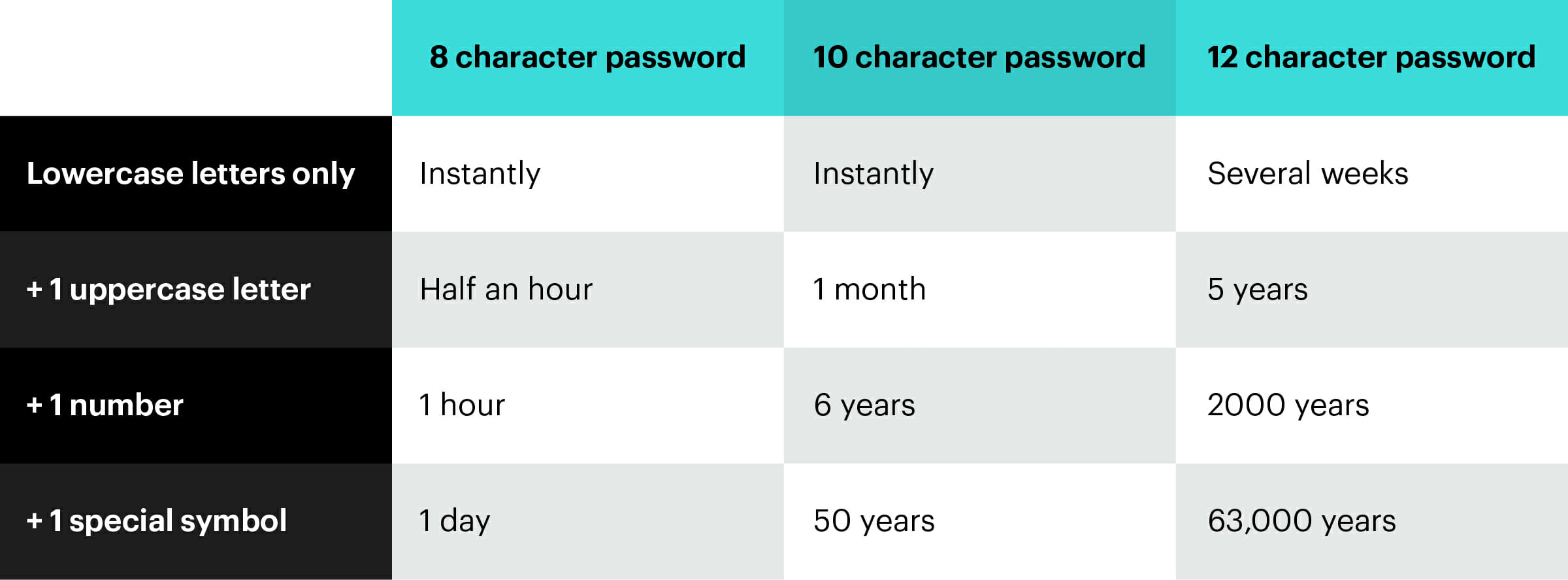
A password, of course. You use them every day, and probably think you have a dozen or so. Actually, research by password manager NordPass shows that a typical user has around 100 passwords. No wonder we find them all impossible to remember.
Actually, you’re almost certainly safer if you can’t remember your password, as memorable words and phrases are all too easy to hack. Only strong passwords offer any security, but many of us still don’t use strong passwords.
Using a password that’s easy to remember or easy to guess is a bad idea. If one of your important passwords is hacked, cracked or stolen the consequences can be costly. An easy to remember password solves one problem – your login frustrations – yet causes another.
A better solution could be a password notebook. Yes, a real honest-to-goodness paper and pen notebook. It’s an analogue solution, so it’s un-hackable. What could go wrong? Well, you could lose it. Or worse, leave it in a public place. It could be stolen, or copied without your knowledge.
So just what is a strong password? Consider these two examples, each containing six numbers and five letters, with one capital letter. Are they equally strong? I’ll give you a clue – one is a date and name and one is a randomly generated sequence.
- 768071htimS
- 948582rzypQ
Both are examples of passwords that are difficult to hack with brute force (further description of brute hacks below). But the first is a name “Smith” and a date “17 08 67” typed backwards. It’s a fictional example, but let’s say that’s your mother’s maiden name and her date-of-birth. Easy for you to remember, so that’s good. But is your mother on Facebook? Is her account connected to yours? Then all that information is accessible to the public, potentially. Hackers, scammers, criminals and general ne’er-do-wells are on the lookout for this kind of information. They can use it to build a database of your information and try to hack your accounts remotely.